Blog

Do Your Employees Have the Right Cybersecurity Training?
Have you ever wondered if your employees are truly prepared to defend against cyber threats? With cyberattacks growing more sophisticated, it's crucial that your team is equipped to handle these challenges. Employees are often the first line of defense, and their...

Password Best Practices to Protect Your Business
You’ve likely heard that “Password123” isn’t a strong password and that using easily guessable information like your last name is a bad idea, but do you know why? We have the answer for you: dictionary attacks. Dictionary attacks are a brute force method used by...
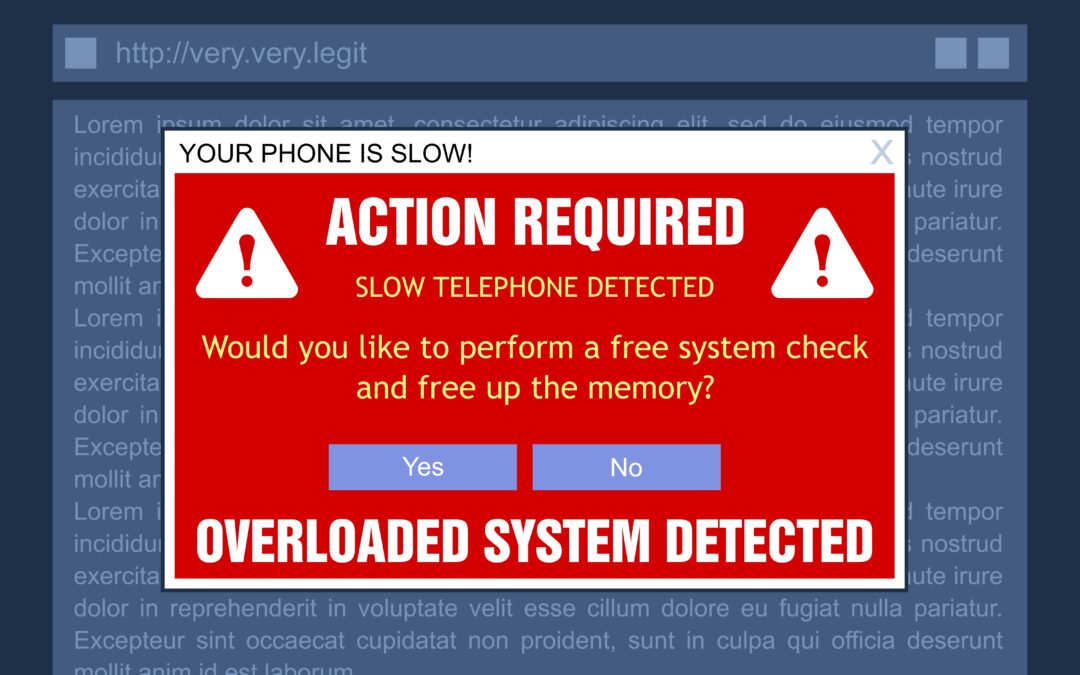
Help! How Do You Deal With Tech Pop-Up Scams?
Has a blaring pop-up claiming a virus or offering an unbelievable prize ever interrupted your browsing? You've likely faced a tech pop-up scam. These online traps are becoming increasingly common, preying on the fear and trust of Long Island residents and internet...

How To Outsmart Phishing Scams and Protect Your Business
Phishing attacks and email scams can feel like a minefield, especially if you’re not sure what to watch out for. Those sneaky emails can blend in with real ones, making it tough to tell what's safe. They might try to rush you, tempt you with deals, or even scare you...

Locking Up Cyber-security with a Managed Services Provider
Cybercrime is not the most costly of illegal activities. That dubious distinction goes to government corruption, followed by drug trafficking. Cybercrime comes in third. Yet cybercrime does take the top spot when it comes to numbers of victims. A managed services...

11 Reasons To Upgrade To Office 365 Today
With Office 365, it seems common sense has finally prevailed, giving business the changes they actually want. It’s still Office, and your staff will still know exactly how to work it, but they’ll get so much more done. 1. The whole Mac/Windows drama is over Office 365...

5 Red Flags of Phishing Emails: Think Before You Click
A single click can be the difference between maintaining data security and suffering massive financial losses. From the moment just one employee takes the bait in a phishing email, your business is vulnerable to data breaches and extensive downtime. Quickly spot the...

Why Your Small Business Needs VoIP
Why would a small business need VoIP? Not just another acronym to learn, Voice over Internet Protocol (VoIP) offers many advantages for small business. Especially SMBs that want to run with the enterprise-sized companies. Basically, VoIP turns voice conversation into...

Got a Bad Case of Password Exhaustion?
You’re not alone! Most people use the same password everywhere – home, work, Gmail, Facebook… even for banking. Considering how many passwords we’re expected to remember and use on a daily basis, password exhaustion is a very real thing. It’s no wonder that when yet...

Top 5 Cloud Advantages for Small Business
Cloud technology has created a revolution for small business, changing the way you store, share and backup files. While ‘the cloud’ is often hard to understand because it’s neither in the sky or in a single location, there’s no arguing that it’s driving growth across...
